
 Flexible
Flexible
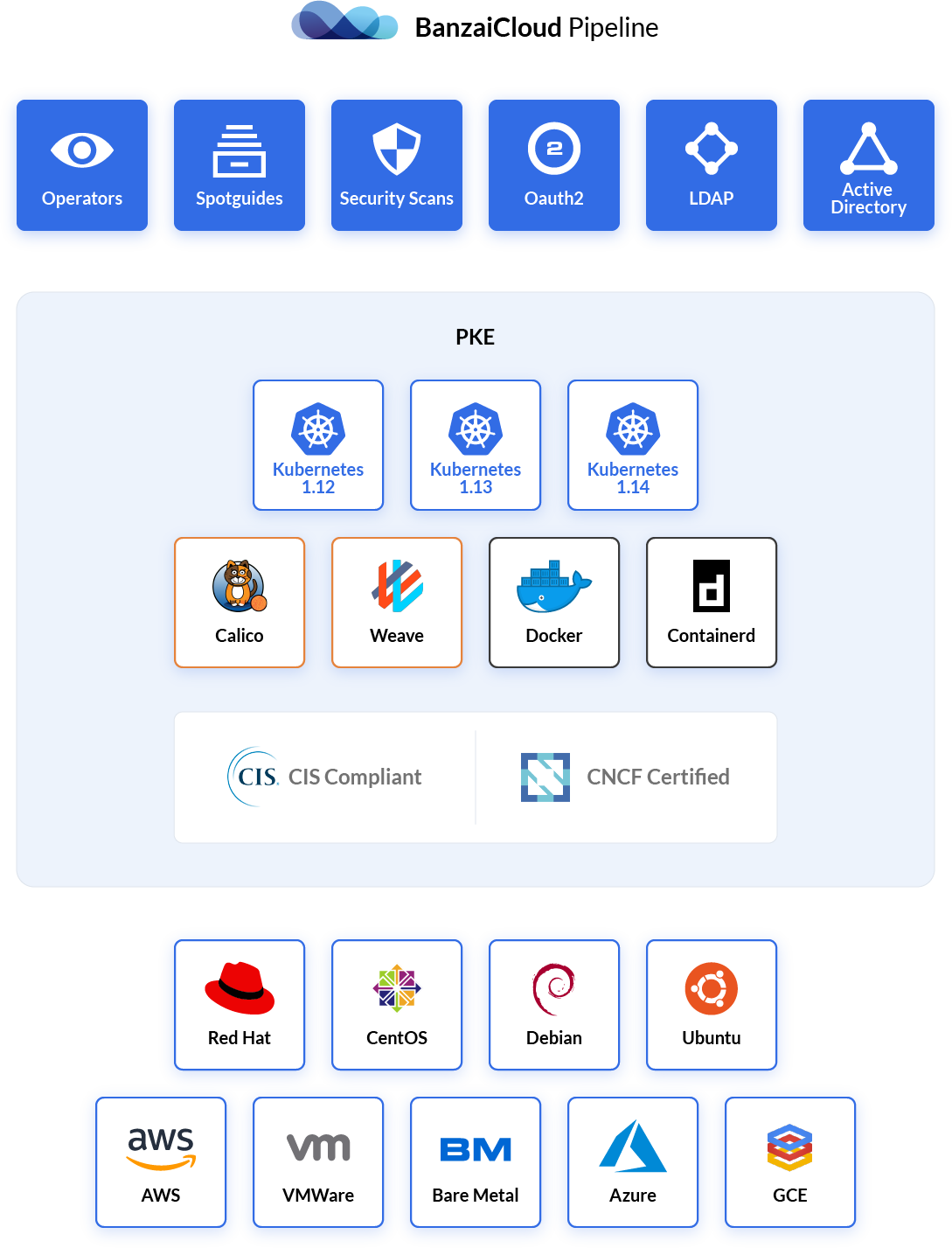
You have full control over the Kubernetes settings. Integrate your corporate authentication for administrative access easily.
 Multi-cloud
Multi-cloud
Deploy your applications to the same environment even if they are hosted at different cloud providers, on-prem, or both.
 Secure
Secure
PKE is designed with enterprise security requirements in mind. Unlike popular hosted solutions, PKE meets the criteria of the CIS benchmark.
PKE is always built based on the latest vanilla Kubernetes version with all the available features and security patches. Using PKE tool you can deploy your own Kubernetes cluster with a single command. You can choose between Docker and ContainerD runtimes, and use your preferred implementation of container networking.
PKE is hardened to pass the CIS security benchmark by default: Role based access control (RBAC) is enabled, and battle-tested Pod Security Policies and Network Policies are built in and available for everyone. The cluster components use TLS for in-cluster communication as well.
Adding Pipeline to the stack extends the capabilities even further with deployments, CI/CD workflow, key management, secret store, logging, monitoring, service mesh and many more.
Our mission at Banzai Cloud is to make the digital transformation of tech companies to the Cloud Native era as …
Read more
Government organizations and institutions have similar requirements and goals regarding their IT infrastructure as …
Read more
A generation of system engineers has grown up who’ve never had to go to a data center as part of their job. …
Read more