In one of our previous posts about creating Helm Charts for Kubernetes, we outlined what we consider the best practices for creating Helm charts. We’ve been using Helm in production and investing our time in creating Helm charts (available on the Banzai Cloud Charts GitHub repository) since Banzai Cloud’s inception. Creating Helm Charts is one thing; storing and serving them is another. We’d like to reduce the burden this places on the user, so today marks the launch of our chart repository, which you can use to store and serve public Helm Charts for free.
tl;dr: 🔗︎
- Accessing the Banzai Cloud chart repository
- We opensourced a Chartsec library, making it available as a Golang lib or CLI tool
- As part of Pipeline’s enterprise version, we support private Helm Chart repositories
- The chart repository is available for free, with a generous fair usage policy
Architecture 🔗︎
Our Helm Chart service is based on ChartMuseum, an open-source, easy to deploy, Helm Chart repository server. We are using the upstream ChartMuseum distribution without any modifications. We have, however, added certain features to make it a managed, multi-tenant service.
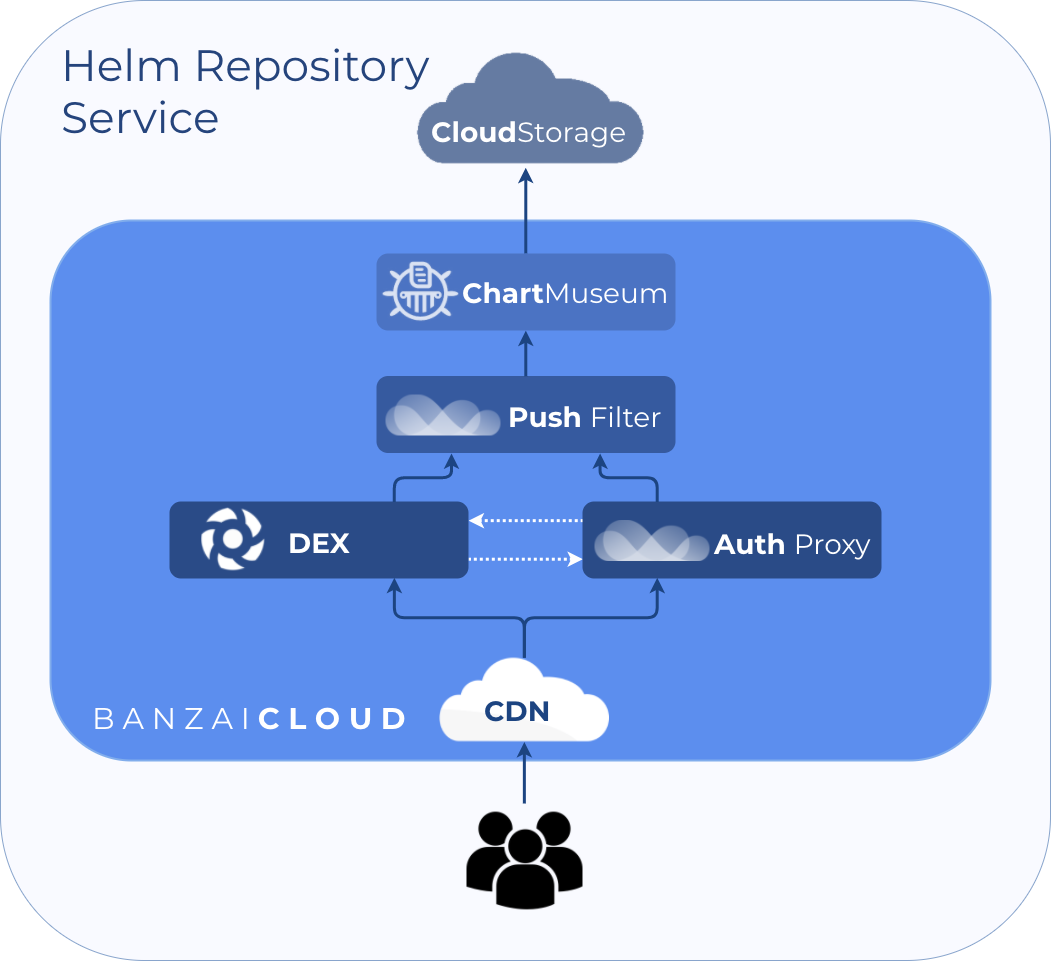
The services we added are outlined below:
Authentication Service 🔗︎
Pulling charts from our Chart repository service doesn’t require authentication (in the free version), but pushing charts to the repository is protected by user authentication. You must request an API token - the free version supports GitHub, GitLab or BitBucket authentication - before you can receive the access necessary to push charts to the repositories of organizations/teams on a given provider. Our enterprise version supports private chart repositories, where chart access is protected.
NOTE: if you are not part of an organization/team on a given SCM provider, it is not possible for you to use the Chart service at this time.
An API token will be created by the official ChartMuseum/auth Go library.
Chart Push Filter 🔗︎
The Chart Push Filter scans charts and compares them to sets of XSS policies and quota limits. For this, we use a version of UGCPolicy from the widely venerated bluemonday Go library with some added quota checks and with the Chartsec library, which we open-sourced and is also used as part of our Pipeline project.
Usage 🔗︎
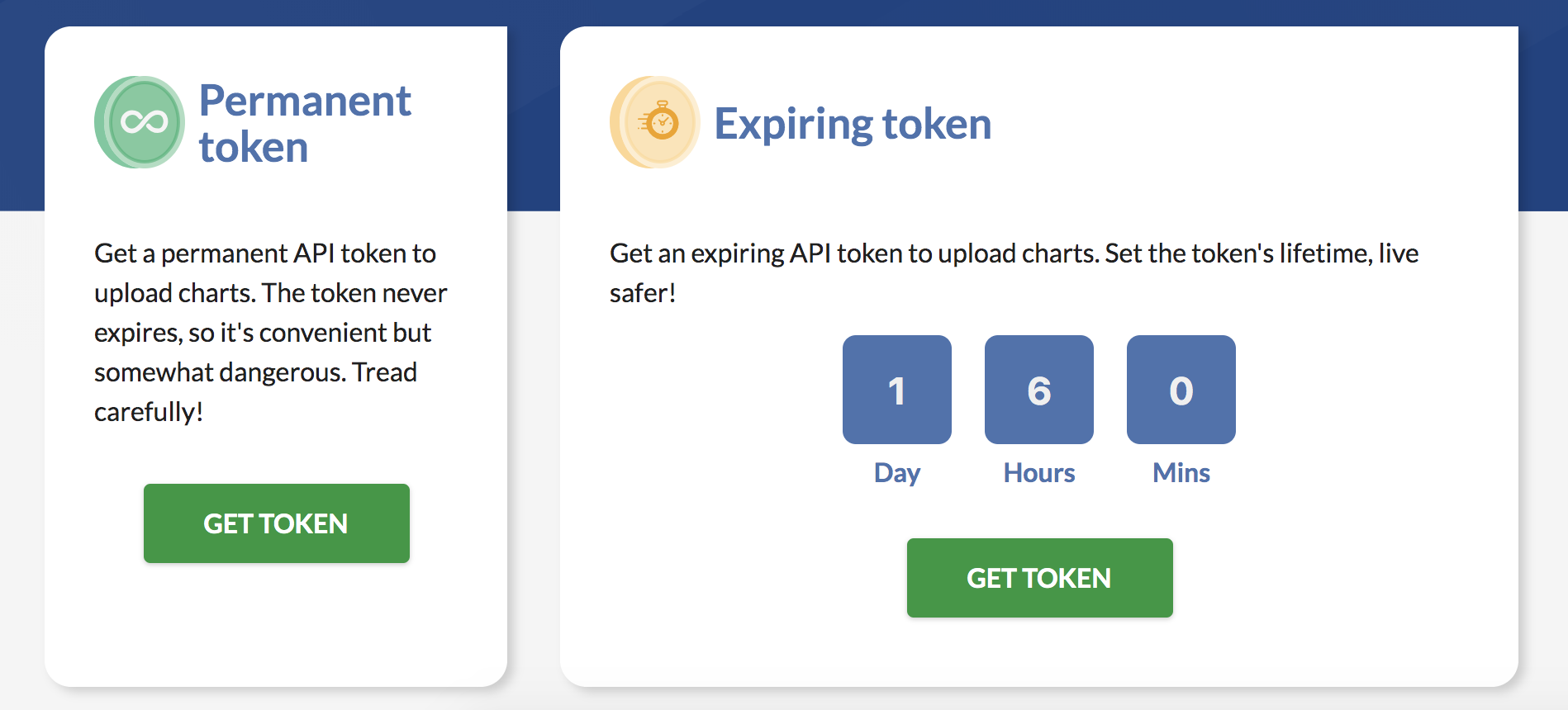
To get a repository for your organization/team, navigate to the Banzai Cloud chart repository and request an API token, then choose between expiring and non-expiring tokens:
After requesting an API token, you will land on a page with instructions for using the Chart repository service in an end user-specific way. The outlined instructions will be very similar to those in the Helm Push Plugin documentation:
Install the Push plugin:
$ helm plugin install https://github.com/chartmuseum/helm-pushExpose the ChartMuseum API token in your shell, so the push plugin can pick it up:
$ export HELM_REPO_ACCESS_TOKEN="eyJhbGciOiJSUz..."Add the new repository to your Helm configuration (in my case it’s gh/banzaicloud, which belongs to the https://github.com/banzaicloud GitHub organization):
$ helm repo add my-helm-repo cm://charts.banzaicloud.io/gh/banzaicloudPush one of your charts into the newly added repository:
$ helm push my-helm-chart-0.1.2.tgz my-helm-repo
Pushing my-helm-chart-0.1.2.tgz to my-helm-repo...
Done.CircleCI Helm Orb 🔗︎
We have also created a Helm CircleCI Orb, which can be reused in your CircleCI configurations. This Orb helps you streamline and automate the steps involved with:
- configuring dependent repositories
- linting and checking
- packaging
- and publishing a Helm chart to a configurable Helm repository.
We’ve assembled a simple Go Hello World application packaged as a Helm Chart, as well, which uses the Helm Orb for demonstration purposes. Here’s how:
version: 2.1
orbs:
helm: banzaicloud/helm@volatile
jobs:
build:
docker:
- image: circleci/golang:1.12
environment:
GOFLAG: -mod=readonly
steps:
- checkout
- run:
name: Build
command: |
go build
workflows:
e2e-test:
jobs:
- build
helm-chart:
jobs:
- helm/publish-chart:
# The `helm-banzaicloud` Circle Context has to exist which
# contains the HELM_REPO_ACCESS_TOKEN from above, you have
# to create this manually after you have requested a token.
# See: https://circleci.com/docs/2.0/contexts/
context: helm-banzaicloud
chart-path: charts/simple-helm-app
# Your own Banzai Cloud Chart repository URL, in my case
# the one belonging to the banzaicloud GitHub organization.
chartmuseum-url: cm://charts.banzaicloud.io/gh/banzaicloud
filters:
branches:
ignore: /.*/
tags:
only: /simple-helm-app\/\d+.\d+.\d+/(No blog about Kubernetes is complete without a wall of YAML, but at least there’s no Kubernetes manifests this time)
From the description above, you can see that tagging the application with the simple-helm-app/0.1.0 tag, for example, triggers the chart packaging, as can be seen in this build job.
Usage policy 🔗︎
Our chart repository is free for everyone to use, with the fair use policy highlighted below:
- Compressed uploaded charts shouldn’t exceed 100k bytes
- Chart packages should contain only those files necessary for the application itself
- Charts should be valid Helm Charts
- Overall, chart storage should not exceed 1GB (this is around 100 charts with about 100 versions of each chart)
If you have different needs, would like to deploy this chart within your environment, or have any other questions, contact us.
Enterprise offering 🔗︎
All this comes as part of the Pipeline Enterprise package, with which we offer a secure Chart repository service for all users, out-of-the-box, allowing users to create secure, private chart repositories, with no limitations.
Learn more about Helm:
About Banzai Cloud Pipeline 🔗︎
Banzai Cloud’s Pipeline provides a platform for enterprises to develop, deploy, and scale container-based applications. It leverages best-of-breed cloud components, such as Kubernetes, to create a highly productive, yet flexible environment for developers and operations teams alike. Strong security measures — multiple authentication backends, fine-grained authorization, dynamic secret management, automated secure communications between components using TLS, vulnerability scans, static code analysis, CI/CD, and so on — are default features of the Pipeline platform.














