In this scenario, Vault runs outside an Istio mesh, whereas the namespace where the application runs and the webhook injects secrets has Istio sidecar injection enabled.
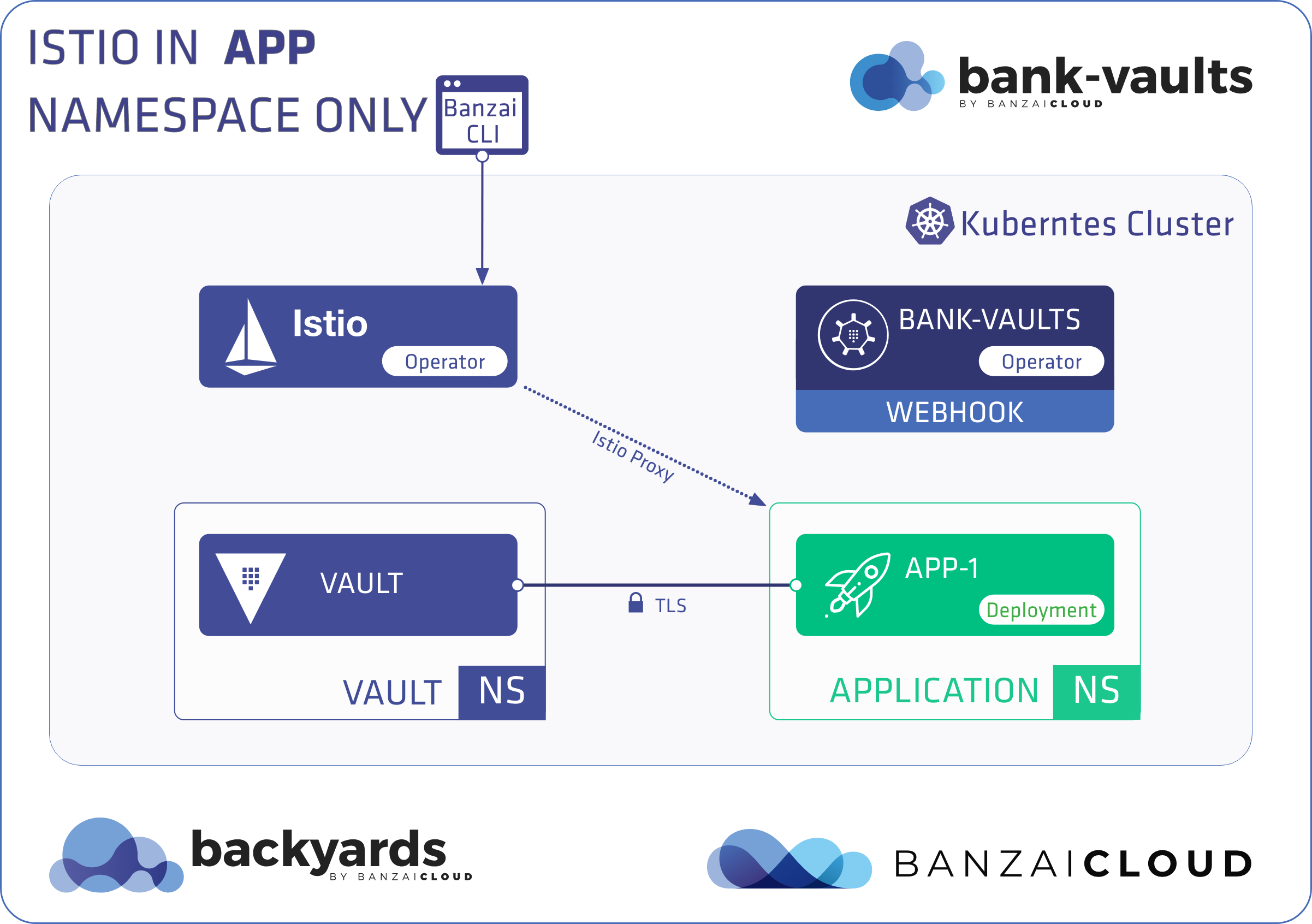
First, complete the Prerequisites, then install Vault outside the mesh, and finally install an application within the mesh.
Install Vault outside the mesh 🔗︎
-
Provision a Vault instance with the Bank-Vaults operator in a separate namespace:
kubectl create namespace vault -
Apply the RBAC and CR files to the cluster to create a Vault instance in the
vaultnamespace with the operator:kubectl apply -f rbac.yaml -f cr-istio.yaml$ kubectl get pods -n vault NAME READY STATUS RESTARTS AGE vault-0 3/3 Running 0 22h vault-configurer-6458cc4bf-6tpkz 1/1 Running 0 22hIf you are writing your own Vault CR make sure that
istioEnabled: trueis configured, this influences port naming so the Vault service port protocols are detected by Istio correctly. -
The
vault-secrets-webhookcan’t inject Vault secrets intoinitContainersin an Istio-enabled namespace when theSTRICTauthentication policy is applied to the Vault service, because Istio needs a sidecar container to do mTLS properly, and in the phase wheninitContainersare running the Pod doesn’t have a sidecar yet. If you wish to inject intoinitContainersas well, you need to apply aPERMISSIVEauthentication policy in thevaultnamespace, since it has its own TLS certificate outside of Istio scope (so this is safe to do from networking security point of view).-
With
kubectl:$ kubectl apply -f - <<EOF apiVersion: authentication.istio.io/v1alpha1 kind: Policy metadata: name: default namespace: vault labels: app: security spec: peers: - mtls: mode: PERMISSIVE EOF -
With
backyards:$ backyards mtls allow vault INFO[0001] policy peers for vault/ set successfully mTLS rule for vault/ Policy Targets MtlsMode vault/default [] PERMISSIVE
-
Install the application inside a mesh 🔗︎
In this scenario Vault is running outside the Istio mesh (as we have installed it in the previous steps and our demo application runs within the Istio mesh. To install the demo application inside the mesh, complete the following steps:
-
Create a namespace first for the application and enable Istio sidecar injection:
kubectl create namespace app-
With
kubectl:kubectl label namespace app istio-injection=enabled -
With
backyards:backyards sidecar-proxy auto-inject on app
-
-
Install the application manifest to the cluster:
kubectl apply -f app.yaml -
Check that the application is up and running. It should have two containers, the
appitself and theistio-proxy:$ kubectl get pods -n app NAME READY STATUS RESTARTS AGE app-5df5686c4-sl6dz 2/2 Running 0 119s$ kubectl logs -f -n app deployment/app app time="2020-02-18T14:26:01Z" level=info msg="Received new Vault token" time="2020-02-18T14:26:01Z" level=info msg="Initial Vault token arrived" s3cr3t going to sleep...











