The Vault operator builds on Bank-Vaults features such as:
- external, API based configuration (secret engines, auth methods, policies) to automatically re/configure a Vault cluster
- automatic unsealing (AWS, GCE, Azure, Alibaba, Kubernetes Secrets (for dev purposes), Oracle)
- TLS support
The operator flow is the following:
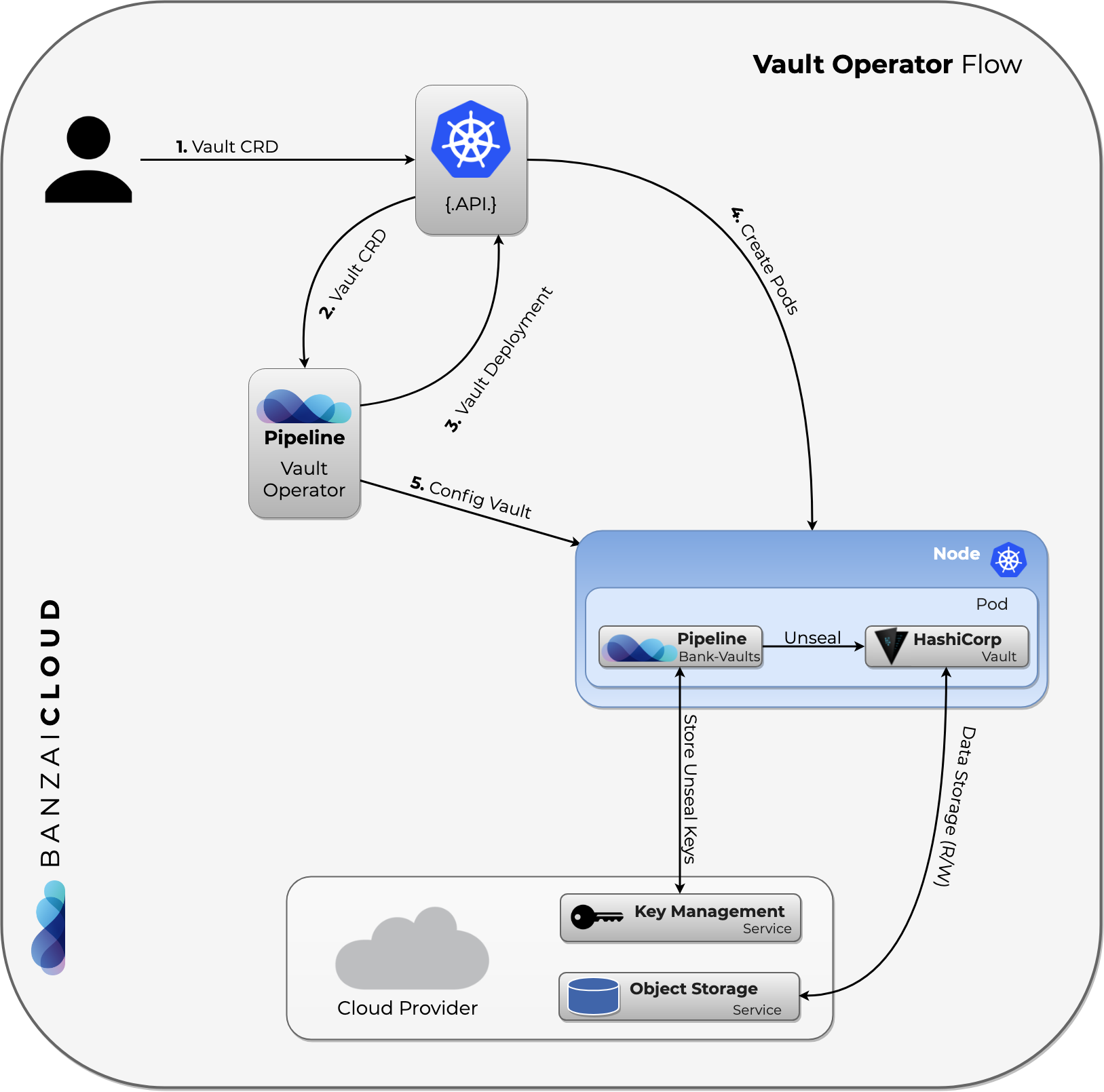
The source code can be found in the operator directory.
The operator requires the following cloud permissions.
Deploy a local Vault operator 🔗︎
This is the simplest scenario: you install the Vault operator on a simple cluster. The following commands install a single-node Vault instance that stores unseal and root tokens in Kubernetes secrets.
-
Install the Bank-Vaults operator:
helm repo add banzaicloud-stable https://kubernetes-charts.banzaicloud.com helm upgrade --install vault-operator banzaicloud-stable/vault-operator -
Create a Vault instance using the Vault custom resources. This will create a Kubernetes
CustomResourcecalledvaultand a PersistentVolumeClaim for it:kubectl apply -f https://raw.githubusercontent.com/banzaicloud/bank-vaults/master/operator/deploy/rbac.yaml kubectl apply -f https://raw.githubusercontent.com/banzaicloud/bank-vaults/master/operator/deploy/cr.yaml -
Wait a few seconds, then check the operator and the vault pods:
kubectl get pods NAME READY STATUS RESTARTS AGE vault-0 3/3 Running 0 10s vault-configurer-6c545cb6b4-dmvb5 1/1 Running 0 10s vault-operator-788559bdc5-kgqkg 1/1 Running 0 23s -
Configure your Vault client to access the Vault instance running in the vault-0 pod.
-
Port-forward into the pod:
kubectl port-forward vault-0 8200 & -
Set the address of the Vault instance.
export VAULT_ADDR=https://127.0.0.1:8200 -
Import the CA certificate of the Vault instance by running the following commands (otherwise, you’ll get x509: certificate signed by unknown authority errors):
kubectl get secret vault-tls -o jsonpath="{.data.ca\.crt}" | base64 --decode > $PWD/vault-ca.crt export VAULT_CACERT=$PWD/vault-ca.crtAlternatively, you can instruct the Vault client to skip verifying the certificate of Vault by running:
export VAULT_SKIP_VERIFY=true -
Check that you can access the vault:
$ vault status Key Value --- ----- Seal Type shamir Initialized true Sealed false Total Shares 5 Threshold 3 Version 1.5.4 Cluster Name vault-cluster-27ecd0e6 Cluster ID ed5492f3-7ef3-c600-aef3-bd77897fd1e7 HA Enabled false -
To authenticate to Vault, you can access its root token by running:
export VAULT_TOKEN=$(kubectl get secrets vault-unseal-keys -o jsonpath={.data.vault-root} | base64 --decode)Note: Using the root token is recommended only in test environments. In production environment, create dedicated, time-limited tokens.
-
Now you can interact with Vault. For example, add a secret by running
vault kv put secret/demosecret/aws AWS_SECRET_ACCESS_KEY=s3cr3tIf you want to access the Vault web interface, open https://127.0.0.1:8200 in your browser using the root token (to reveal the token, runecho $VAULT_TOKEN).
-
For other configuration examples of the Vault CustomResource, see the YAML files in the operator/deploy directory of the project (we use these for testing), and our various blog posts. After you are done experimenting with Bank-Vaults and you want to delete the operator, you can delete the related CRs:
kubectl delete -f https://raw.githubusercontent.com/banzaicloud/bank-vaults/master/operator/deploy/rbac.yaml
kubectl delete -f https://raw.githubusercontent.com/banzaicloud/bank-vaults/master/operator/deploy/cr.yaml
HA setup with Raft 🔗︎
In a production environment you want to run Vault as a cluster. The following CR creates a 3-node Vault instance that uses the Raft storage backend:
-
Install the Bank-Vaults operator:
helm repo add banzaicloud-stable https://kubernetes-charts.banzaicloud.com helm upgrade --install vault-operator banzaicloud-stable/vault-operator -
Create a Vault instance using the
cr-raft.yamlcustom resource. This will create a KubernetesCustomResourcecalledvaultthat uses the Raft backend:kubectl apply -f https://raw.githubusercontent.com/banzaicloud/bank-vaults/master/operator/deploy/rbac.yaml kubectl apply -f https://raw.githubusercontent.com/banzaicloud/bank-vaults/master/operator/deploy/cr-raft.yaml
CAUTION:
Backing up the storage backend to prevent data loss, is not handled by the Vault operator. We recommend using Velero for backups.Pod anti-affinity 🔗︎
If you want to setup pod anti-affinity, you can set podAntiAffinity vault with a topologyKey value.
For example, you can use failure-domain.beta.kubernetes.io/zone to force K8S deploy vault on multi AZ.
Delete a resource created by the operator 🔗︎
If you manually delete a resource that the Bank-Vaults operator has created (for example, the Ingress resource), the operator automatically recreates it every 30 seconds. If it doesn’t, then something went wrong, or the operator is not running. In this case, check the logs of the operator.











