An Istio service mesh has a few different ways of reaching services that are external to the mesh. External services are everything that are not defined in Istio’s internal service registry, that is, services which are outside of the mesh. By default Istio configures the Envoy proxy to passthrough requests for unknown or external services.
Depending on backyards istio outbound-traffic-policy [allowed|restricted], all traffic to external services is permitted or forbidden. While using permissive configuration for testing purposes is ok, in a production environment a stricter configuration might be necessary. In both cases there are situations where you want to have control over your external traffic.
Backyards is using Istio’s - and therefore Envoy’s - egress control feature under the hood.
Configure access to external services from the command line 🔗︎
Before you begin, make sure that at least a single cluster mesh is set up properly.
Change the default policy 🔗︎
You can change the default policy for outbound traffic by running the backyards istio outbound-traffic-policy <setting> command. For example, to restrict outbound traffic to the known endpoints, run the following command.
$ backyards istio outbound-traffic-policy restricted
Expected output:
mesh wide outbound traffic policy is set to 'REGISTRY_ONLY'
Create a service entry for an external service 🔗︎
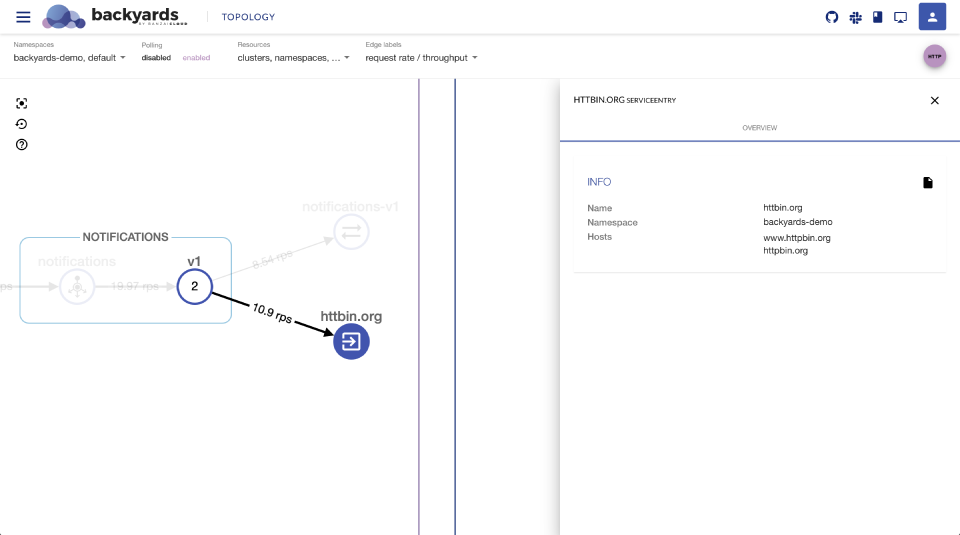
The following command creates a service endpoint for httpbin.org, a simple HTTP Request & Response Service.
$ kubectl apply -f - <<EOF
apiVersion: networking.istio.io/v1alpha3
kind: ServiceEntry
metadata:
name: httpbin.org
namespace: backyards-demo
spec:
hosts:
- httpbin.org
- www.httpbin.org
ports:
- number: 80
name: http
protocol: HTTP
resolution: DNS
location: MESH_EXTERNAL
EOF
After you issue the command, modify the notifications deployment to call httpbin.org
Accessing external HTTPS services comes with a few constrains.
- All the HTTP-related information like method, URL path, response code, is encrypted so Istio cannot see and cannot monitor that information for HTTPS.
- Backyard’s dashboard shows HTTPS as TCP since detailed HTTP-related information is not available.
Calling external service from notifications deployment 🔗︎
$ kubectl -n backyards-demo set env deployment/notifications-v1 'REQUESTS=http://httpbin.org/get#1'
deployment.extensions/notifications-v1 env updated
Once the notifications pods are restarted, the Backyards Dashboard will display outgoing calls to httpbin.org
Cleanup 🔗︎
Restore notifications service to not to call external service.
$ kubectl -n backyards-demo set env deployment/notifications-v1 'REQUESTS-'
deployment.extensions/notifications-v1 env updated
Remove service entry for httpbin.org
$ kubectl delete serviceentry -n backyards-demo httpbin.org
serviceentry.networking.istio.io "httpbin.org" deleted
Restore outbound traffic policy to permissive.
$ backyards istio outbound-traffic-policy allowed
mesh wide outbound traffic policy is set to 'ALLOW_ANY'