Backyards understands Istio’s Gateway CRs and the gateway’s service configuration in Kubernetes (with the help of the MeshGateway CR), so it can display information about ports, hosts, and protocols that are configured on a specific gateway.
-
Open the Backyards web interface, and navigate to MENU > GATEWAYS.
-
From the list of gateways, click the gateway you want to monitor.
-
You can see the host and port configurations on the OVERVIEW tab, in the Ports & Hosts section.
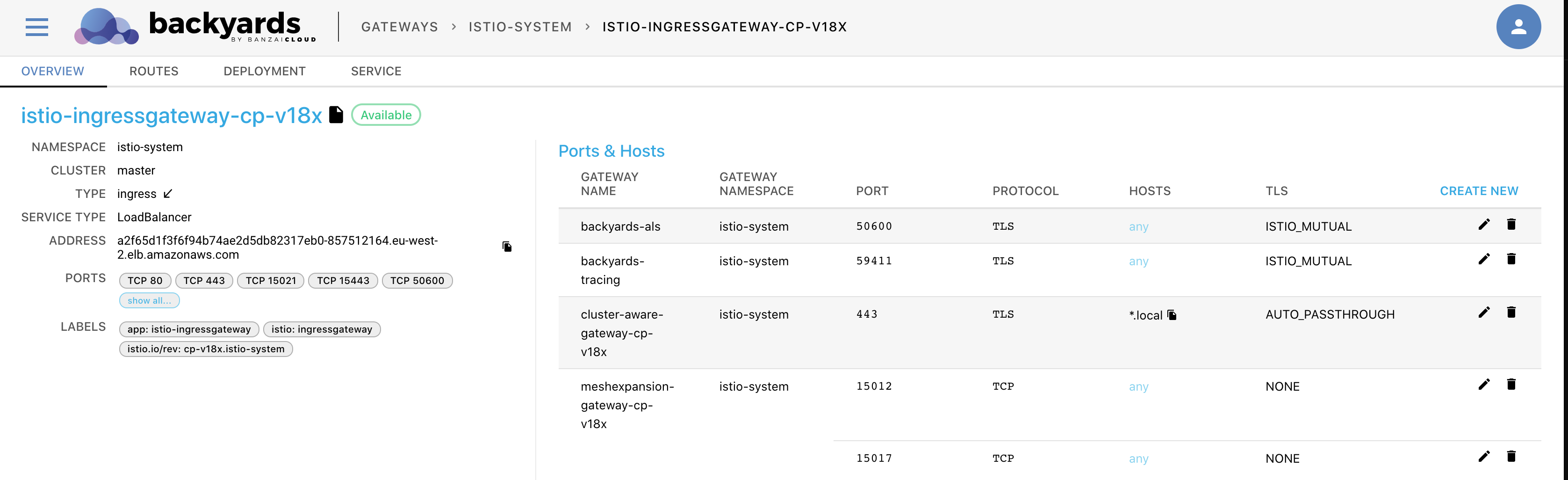
The following information is shown about each entry point.
- GATEWAY NAME: The name of the gateway.
- GATEWAY NAMESPACE: The namespace the gateway belongs to.
- PORT: The list of open ports on the gateway.
- PROTOCOL: The protocols permitted on the gateway.
- HOSTS: The host selector that determines which hosts are accessible using the gateway.
- TLS: The TLS settings applying to the gateway.
- To modify an existing route, click
, change the settings as needed, then click APPLY.
- To delete a route, click
 .
. - To create a new entry point, click CREATE NEW.
Create new ingress entry point 🔗︎
You can also set up a new entry point for your Istio ingress gateways, and Backyards will translate your configuration to declarative custom resources.
-
Navigate to MENU > GATEWAYS > <Gateway-to-modify> > OVERVIEW.
-
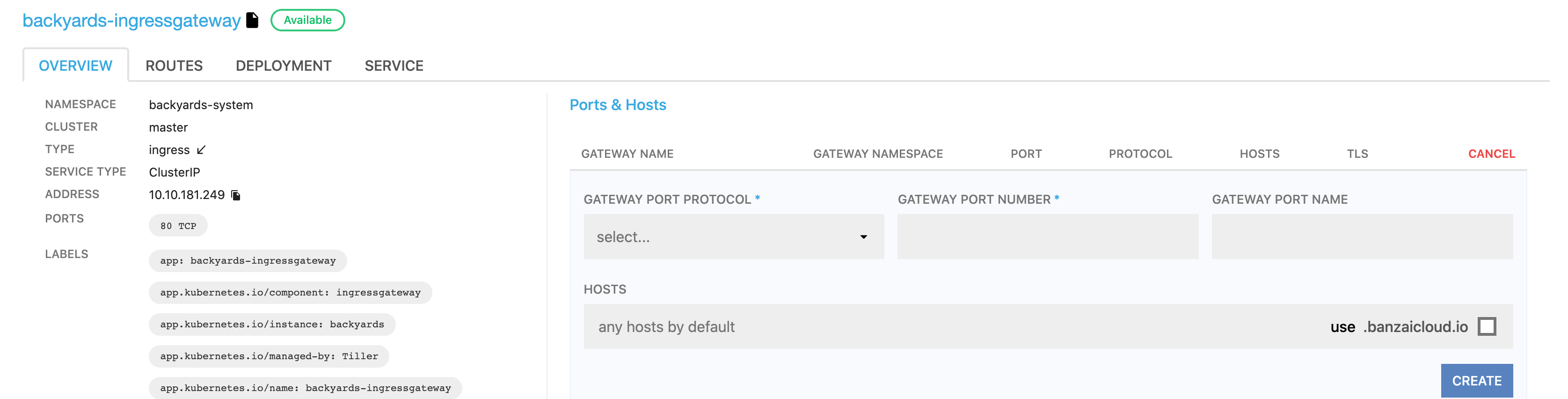
In the Ports & Hosts section click CREATE NEW.
-
Set the parameters of the entry point.
Note: DNS resolution is not managed by Backyards. Once you’ve configured ingress for a particular service, Backyards will display the IP of the ingress gateway service. Do not forget to create the corresponding DNS records that point to this IP. Alternatively, select the use .banzaicloud.io option to have an automatic domain name entry under the banzaicloud.io domain.
-
Click CREATE.
Gateway TLS settings 🔗︎
When setting up a service on a gateway with TLS, you need to configure a certificate for the host(s). You can do that by bringing your own certificate, putting it down in a Kubernetes secret, and configuring it for a gateway server. This works for simple use cases, but involves lots of manual steps when obtaining or renewing a certificate. Automated Certificate Management Environments (ACME) automates these kinds of interactions with the certificate provider.
ACME is most widely used with Let’s Encrypt and - when in a Kubernetes environment - cert-manager. Backyards (now Cisco Service Mesh Manager) helps you set up cert-manager, and you can quickly obtain a valid Let’s Encrypt certificate through the dashboard with a few clicks - even with a banzaicloud.io domain automatically if you’d like.
Note: For details on using your own domain name with Let’s Encrypt, see Using Let’s Encrypt with your own domain name.
To set TLS encryption for a gateway, complete the following steps.
-
Navigate to MENU > GATEWAYS > <Gateway-to-modify> > OVERVIEW.
-
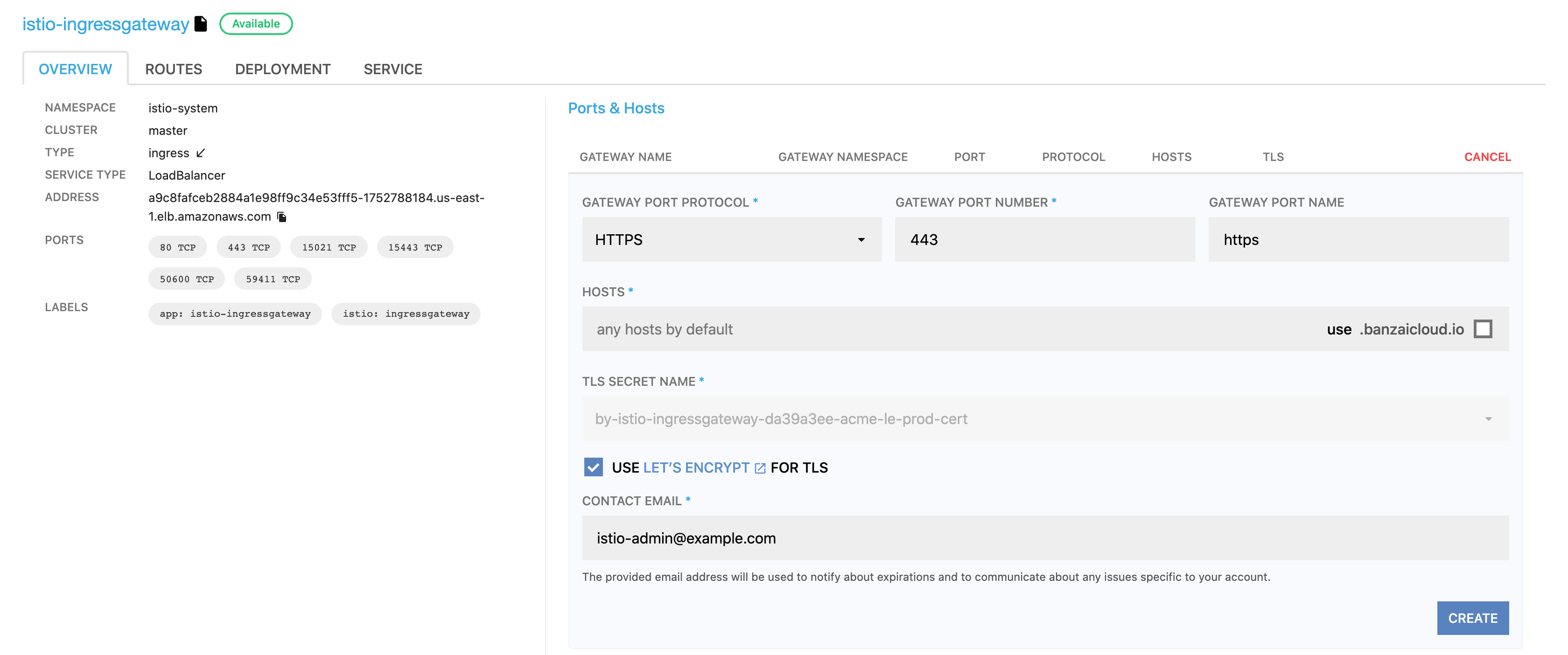
In the Ports & Hosts section, click
in the row of the gateway you want to modify.
-
Set GATEWAY PORT PROTOCOL to HTTPS.
-
Select USE LET’S ENCRYPT FOR TLS.
-
Enter a valid email address. The provided email address will be used to notify about expirations and to communicate about any issues specific to your account.
-
Click CREATE.













