By default, each Envoy proxy receives information about every workload in the mesh. This can result in high memory usage in the Envoy proxies. Backyards can help you limit the allowed outbound connections of a workload or a whole namespace to reduce the memory requirements, especially in larger meshes.
You can set a restriction manually, or you can rely on Backyards to give you a recommended configuration based on the current network traffic. For details on how this works, see our blog post about the sidecar resource.
Backyards is using Istio’s - and therefore Envoy’s - sidecar feature under the hood.
Restrict outbound traffic from the command line 🔗︎
The following sections describe how to manage outbound traffic restrictions using the backyards command-line tool. If you want to use the Backyards web interface instead, see Restrict outbound traffic using the Backyards UI.
Get an outbound traffic restriction recommendation 🔗︎
-
To get a recommendation for a specific workload based on the current traffic, run the following command.
$ backyards sidecar-proxy egress recommend backyards-demo --workload payments-v1Sample output:
Recommended sidecar egress rules for backyards-demo/payments-v1 Sidecar Selector Hosts Bind Port Capture Mode backyards-demo-rmoy8 app="payments" ./notifications.backyards-demo.svc.cluster.local - version="v1" istio-system/istio-telemetry.istio-system.svc.cluster.local Hint: to apply these recommendations, use the --apply switch, or apply it manually using this command: > backyards sp egress set --namespace backyards-demo --workload payments-v1 --hosts='./notifications.backyards-demo.svc.cluster.local' --hosts='istio-system/istio-telemetry.istio-system.svc.cluster.local' -l=app -l=versionIn this case, the recommended configuration only allows connections from the
backyards-demo/payments-v1workload to theistio-telemetryservice in theistio-systemnamespace and to thenotificationsservice in the current namespace (from the perspective of the workload). -
To get a recommendation for the whole namespace (backyards-demo in this case), run the following command.
$ backyards sidecar-proxy egress recommend backyards-demoSample output:
Recommended sidecar egress rules for namespace backyards-demo Sidecar Selector Hosts Bind Port Capture Mode backyards-demo-zy8fq istio-system/* - ./*In this case, the recommendation restricts connections to the current and
istio-systemnamespaces. -
To apply the recommendations, run the same command again with the
--applyswitch, for example:$ backyards sidecar-proxy egress recommend backyards-demo --workload payments-v1 --applyor
$ backyards sidecar-proxy egress recommend backyards-demo --applyAlternatively, you can apply them manually by running the command from the output. For example:
backyards sp egress set --namespace backyards-demo --workload payments-v1 --hosts='./notifications.backyards-demo.svc.cluster.local' --hosts='istio-system/istio-telemetry.istio-system.svc.cluster.local' -l=app -l=versionor
backyards sp egress set --namespace backyards-demo --hosts='istio-system/*' --hosts='./*'
Set an outbound traffic restriction 🔗︎
You can restrict outbound connections to the current namespace using the following command:
$ backyards sp egress set --namespace backyards-demo --hosts='istio-system/*' --hosts='./*'
Expected output:
INFO[0001] sidecar egress for backyards-demo/ set successfully
Sidecar egress rules for namespace backyards-demo
Sidecar Selector Hosts Bind Port Capture Mode
default istio-system/* -
./*
See the IstioEgressListener documentation for the exact format of the --hosts parameter.
Note: it’s necessary to allow connections to the
istio-systemnamespace to use Istio’s policy and telemetry features.
List active outbound traffic restrictions 🔗︎
You can list the currently set outbound traffic restrictions. For example, to get the rules for the backyards-demo/notifications-v1 workload, run the following command:
$ backyards sidecar-proxy egress get backyards-demo --workload notifications-v1
Expected output:
Sidecar egress rules for backyards-demo/notifications-v1
Sidecar Selector Hosts Bind Port Capture Mode
backyards-demo-dhara app="notifications" istio-system/istio-telemetry.istio-system.svc.cluster.local -
version="v1"
Remove outbound traffic restriction 🔗︎
When you do not need the restrictions anymore, you can delete the rules by running the following command:
$ backyards sidecar-proxy egress delete backyards-demo --workload notifications-v1
Expected output:
INFO[0001] sidecar egress for backyards-demo/notifications-v1 deleted successfully
no egress rule found for backyards-demo/notifications-v1
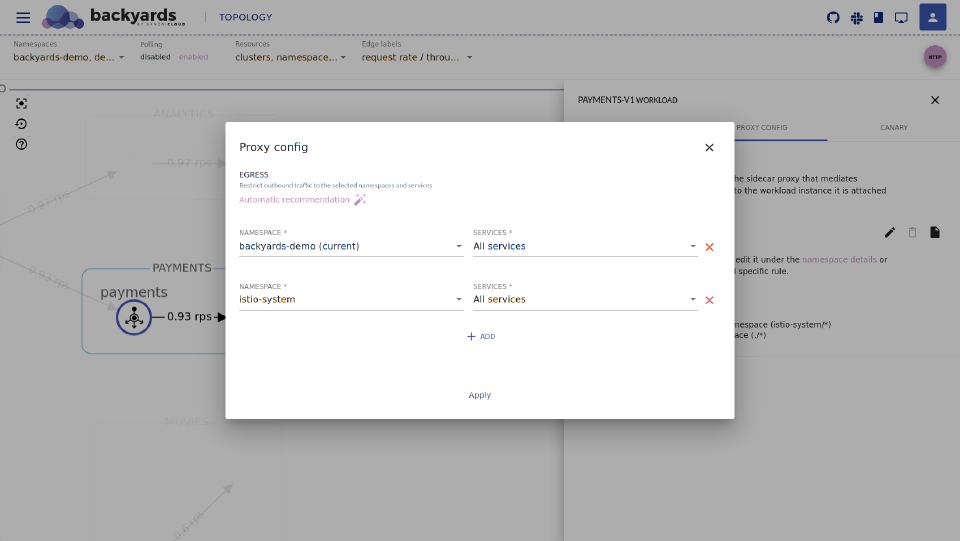
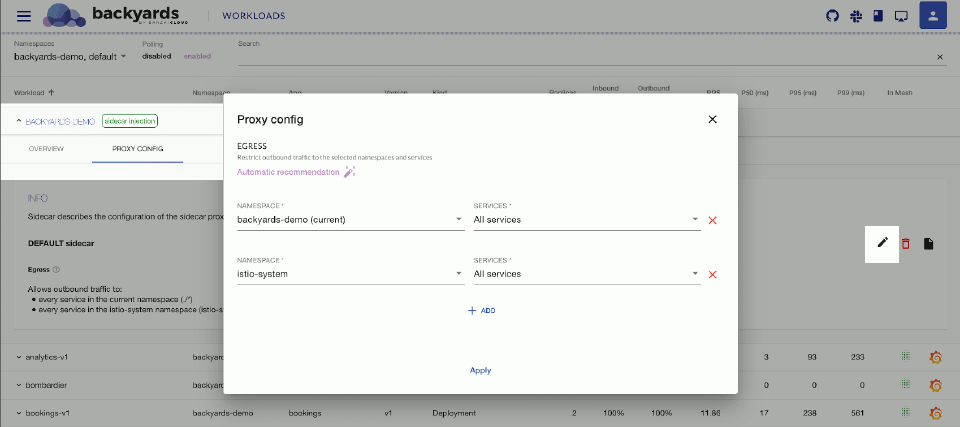
Restrict outbound traffic using the Backyards UI 🔗︎
The following section describes how to manage outbound traffic restrictions using the Backyards web interface. If you want to use the Backyards command line tool instead, see Restrict outbound traffic from the command line .
-
Navigate to
Main menu > WORKLOADS, and click the workload you want to restrict. (You can click on the workload in theTOPOLOGYview as well). -
Click
PROXY CONFIG >.
-
To get rule recommendations based on live traffic, click
Automatic recommendation. -
To add new rule manually, click
ADD. -
To activate your changes, click
Apply. -
To set outbound traffic restrictions for a namespace, click the name of the namespace (shown in capitals, for example, BACKYARDS-DEMO) on the
WORKLOADSview, then clickPROXY CONFIG >.
Note: it’s necessary to allow connections to the
istio-systemnamespace to use Istio’s policy and telemetry features.